示例dump分析:堆内存泄露
代码
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 |
// aet_breakpad_test.cpp : 此文件包含 "main" 函数。程序执行将在此处开始并结束。 // #include <Windows.h> #include <iostream> #include <chrono> #include <stdexcept> #include <thread> #include "client/windows/handler/exception_handler.h" std::wstring get_dump_path() { std::wstring path = L"q:\\dump_repo\\"; return path; } google_breakpad::ExceptionHandler* g_breakpad_handle = nullptr; void init_breakpad() { g_breakpad_handle = new google_breakpad::ExceptionHandler( get_dump_path(), nullptr, nullptr, nullptr, google_breakpad::ExceptionHandler::HANDLER_ALL); } struct MyStruct { int a; int b; }; void Crash() { int x = 99; throw std::runtime_error("Intentional Crash!"); } void (*fn_crash)() = nullptr; int g_test = 666; int main() { init_breakpad(); int a = 0; std::string test = "hello"; std::cout << a << std::endl; MyStruct sttt; sttt.a = 1; sttt.b = 2; int* p1 = new int[10]; MyStruct* pmystr = new MyStruct(); fn_crash = &Crash; const char* cca = "it's me."; char caa[] = {"ready..."}; const wchar_t* wcc = L"我的"; fn_crash(); return 0; } |
分析步骤一
- 在程序启动时,先用下面命令查看堆的情况
!heap -s
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
0:000> !heap -s ************************************************************************************************************************ NT HEAP STATS BELOW ************************************************************************************************************************ NtGlobalFlag enables following debugging aids for new heaps: stack back traces LFH Key : 0x83116615ba8de043 Termination on corruption : ENABLED Heap Flags Reserv Commit Virt Free List UCR Virt Lock Fast (k) (k) (k) (k) length blocks cont. heap ------------------------------------------------------------------------------------- 0000000001cb0000 08000002 1020 36 1020 8 5 1 0 0 0000000000010000 08008000 64 4 64 2 1 1 0 0 ------------------------------------------------------------------------------------- |
!heap -stat -h 1cb0000
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
0:000> !heap -stat -h 1cb0000 heap @ 0000000001cb0000 group-by: TOTSIZE max-display: 20 size #blocks total ( %) (percent of total busy bytes) 1e5a 1 - 1e5a (33.87) 844 1 - 844 (9.22) 400 2 - 800 (8.93) 1d8 4 - 760 (8.23) 100 7 - 700 (7.81) 120 4 - 480 (5.02) 3c0 1 - 3c0 (4.18) 168 2 - 2d0 (3.14) 238 1 - 238 (2.48) a8 3 - 1f8 (2.20) f0 2 - 1e0 (2.09) 50 6 - 1e0 (2.09) 98 3 - 1c8 (1.99) 130 1 - 130 (1.33) 30 6 - 120 (1.26) 40 4 - 100 (1.12) 48 3 - d8 (0.94) 38 3 - a8 (0.73) 42 2 - 84 (0.58) 68 1 - 68 (0.45) |
分析步骤二
g- 让程序跑一会儿
!heap -s- 对比发现Commit多了
128h
- 对比发现Commit多了
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
0:000> !heap -s ************************************************************************************************************************ NT HEAP STATS BELOW ************************************************************************************************************************ NtGlobalFlag enables following debugging aids for new heaps: stack back traces LFH Key : 0x83116615ba8de043 Termination on corruption : ENABLED Heap Flags Reserv Commit Virt Free List UCR Virt Lock Fast (k) (k) (k) (k) length blocks cont. heap ------------------------------------------------------------------------------------- 0000000001cb0000 08000002 1800 164 1020 5 11 1 0 0 LFH 0000000000010000 08008000 64 4 64 2 1 1 0 0 ------------------------------------------------------------------------------------- |
!heap -stat -h 1cb0000
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
0:000> !heap -stat -h 1cb0000 heap @ 0000000001cb0000 group-by: TOTSIZE max-display: 20 size #blocks total ( %) (percent of total busy bytes) 30 cb - 2610 (10.92) 1e5a 1 - 1e5a (8.71) 10 12f - 12f0 (5.43) 1234 1 - 1234 (5.22) 1200 1 - 1200 (5.17) 1034 1 - 1034 (4.65) 1000 1 - 1000 (4.59) 790 2 - f20 (4.34) ed6 1 - ed6 (4.26) 400 3 - c00 (3.44) 120 9 - a20 (2.91) 100 a - a00 (2.87) 844 1 - 844 (2.37) 1d8 4 - 760 (2.12) 706 1 - 706 (2.02) 6d2 1 - 6d2 (1.96) 50 f - 4b0 (1.35) 470 1 - 470 (1.27) 228 2 - 450 (1.24) 168 3 - 438 (1.21) |
观察
- 对比数据发现:
- 新增高频块:
30(48字节)占10.92%,共2610个块,总占用2400字节 - 原最大块
1e5a占比下降:从33.87%降至8.71%,但块数量仍为1个 - 新增大块:
1234(4660字节,5.22%)、1200(4608字节,5.17%) - 碎片化加剧:新增
10(16字节)、120(288字节)等高频小块,总块数达2610个(30尺寸)
- 新增高频块:
- 疑点:
1e5a块:在两份数据中均存在且占用较高,可能是长期未释放的缓存或泄漏对象ed6(3798字节):仅第二份出现,需验证是否为合理分配790(1936字节):新增,第二份中占4.34%,可能关联数组或结构体分配6d2(1746字节):非对齐尺寸,可能因自定义数据结构导致
验证一
- 查看
1e5a
|
1 2 3 4 5 6 |
0:000> !heap -flt s 1e5a _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cb10c0 01e9 0000 [00] 0000000001cb10f0 01e5a - (busy) unknown!printable _HEAP @ 10000 |
|
1 2 3 4 5 6 7 8 9 10 11 12 |
0:000> !heap -p -a 0000000001cb10c0 address 0000000001cb10c0 found in _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cb10c0 01e9 0000 [00] 0000000001cb10f0 01e5a - (busy) unknown!printable 7ffdf53db49d ntdll!RtlpAllocateHeapInternal+0x0000000000000a7d 7ffdf53fb001 ntdll!RtlpInitEnvironmentBlock+0x0000000000000049 7ffdf54828cc ntdll!LdrpInitializeProcess+0x0000000000000b7c 7ffdf5425deb ntdll!LdrpInitialize+0x000000000000015f 7ffdf5425c73 ntdll!LdrpInitialize+0x000000000000003b 7ffdf5425c1e ntdll!LdrInitializeThunk+0x000000000000000e |
- 查看
ed6
|
1 2 3 4 5 |
0:000> !heap -flt s ed6 _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cc5d70 00f0 0000 [00] 0000000001cc5da0 00ed6 - (busy) _HEAP @ 10000 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
0:000> !heap -p -a 0000000001cc5d70 address 0000000001cc5d70 found in _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cc5d70 00f0 0000 [00] 0000000001cc5da0 00ed6 - (busy) 7ffdf53db49d ntdll!RtlpAllocateHeapInternal+0x0000000000000a7d 7ffdf541dac4 ntdll!RtlpComputePath+0x00000000000002f4 7ffdf541d79f ntdll!RtlpComputeDllPath+0x00000000000000cf 7ffdf53c17b1 ntdll!RtlpGetCachedPath+0x00000000000000a9 7ffdf53c15d0 ntdll!LdrpGetDllPath+0x0000000000000154 7ffdf54114c2 ntdll!LdrpComputeLazyDllPath+0x0000000000000052 7ffdf54103c1 ntdll!LdrpSearchPath+0x0000000000000095 7ffdf5410bd6 ntdll!LdrpMapDllSearchPath+0x0000000000000106 7ffdf5410160 ntdll!LdrpProcessWork+0x0000000000000074 7ffdf53cfb53 ntdll!LdrpLoadDllInternal+0x000000000000013f 7ffdf53c73e4 ntdll!LdrpLoadDll+0x00000000000000a8 7ffdf53c6af4 ntdll!LdrLoadDll+0x00000000000000e4 7ffdf2f22612 KERNELBASE!LoadLibraryExW+0x0000000000000162 7ff6139f2a86 aet_breakpad_test!google_breakpad::ExceptionHandler::Initialize+0x0000000000000516 7ff6139efb05 aet_breakpad_test!google_breakpad::ExceptionHandler::ExceptionHandler+0x00000000000000d5 7ff6139ec46c aet_breakpad_test!init_breakpad+0x00000000000000ac 7ff6139e4834 aet_breakpad_test!main+0x0000000000000044 7ff613a72619 aet_breakpad_test!invoke_main+0x0000000000000039 7ff613a724c2 aet_breakpad_test!__scrt_common_main_seh+0x0000000000000132 7ff613a7237e aet_breakpad_test!__scrt_common_main+0x000000000000000e 7ff613a726ae aet_breakpad_test!mainCRTStartup+0x000000000000000e 7ffdf41f7374 KERNEL32!BaseThreadInitThunk+0x0000000000000014 7ffdf53fcc91 ntdll!RtlUserThreadStart+0x0000000000000021 |
- 查看
790
|
1 2 3 4 5 6 7 8 |
0:000> !heap -flt s 790 _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cc4fc0 007c 0000 [00] 0000000001cc4ff0 00790 - (busy) ? ucrtbase!strset+80d0 0000000001cd4b20 007c 007c [00] 0000000001cd4b50 00790 - (busy) ? ucrtbase!strset+80d0 _HEAP @ 10000 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
0:000> !heap -p -a 0000000001cc4fc0 address 0000000001cc4fc0 found in _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cc4fc0 007c 0000 [00] 0000000001cc4ff0 00790 - (busy) ? ucrtbase!strset+80d0 7ffdf53db49d ntdll!RtlpAllocateHeapInternal+0x0000000000000a7d 7ffdf2dfdd3e ucrtbase!calloc_base+0x000000000000004e 7ffdf2e07070 ucrtbase!o_powf+0x00000000000000c0 7ffdf2e07730 ucrtbase!o__recalloc+0x0000000000000150 7ffdf2e06216 ucrtbase!msize+0x0000000000000146 7ffdf53c9a1d ntdll!LdrpCallInitRoutine+0x0000000000000061 7ffdf541d2f7 ntdll!LdrpInitializeNode+0x00000000000001d3 7ffdf541d08a ntdll!LdrpInitializeGraphRecurse+0x0000000000000042 7ffdf541d110 ntdll!LdrpInitializeGraphRecurse+0x00000000000000c8 7ffdf53ed947 ntdll!LdrpPrepareModuleForExecution+0x00000000000000bf 7ffdf53cfbae ntdll!LdrpLoadDllInternal+0x000000000000019a 7ffdf53c73e4 ntdll!LdrpLoadDll+0x00000000000000a8 7ffdf53c6af4 ntdll!LdrLoadDll+0x00000000000000e4 7ffdf2f22612 KERNELBASE!LoadLibraryExW+0x0000000000000162 7ff6139f2a86 aet_breakpad_test!google_breakpad::ExceptionHandler::Initialize+0x0000000000000516 7ff6139efb05 aet_breakpad_test!google_breakpad::ExceptionHandler::ExceptionHandler+0x00000000000000d5 7ff6139ec46c aet_breakpad_test!init_breakpad+0x00000000000000ac 7ff6139e4834 aet_breakpad_test!main+0x0000000000000044 7ff613a72619 aet_breakpad_test!invoke_main+0x0000000000000039 7ff613a724c2 aet_breakpad_test!__scrt_common_main_seh+0x0000000000000132 7ff613a7237e aet_breakpad_test!__scrt_common_main+0x000000000000000e 7ff613a726ae aet_breakpad_test!mainCRTStartup+0x000000000000000e 7ffdf41f7374 KERNEL32!BaseThreadInitThunk+0x0000000000000014 7ffdf53fcc91 ntdll!RtlUserThreadStart+0x0000000000000021 |
- 查看
6d2
|
1 2 3 4 5 6 |
0:000> !heap -flt s 6d2 _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001ccd240 0070 0000 [00] 0000000001ccd270 006d2 - (busy) unknown!printable _HEAP @ 10000 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
0:000> !heap -p -a 0000000001ccd240 address 0000000001ccd240 found in _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001ccd240 0070 0000 [00] 0000000001ccd270 006d2 - (busy) unknown!printable 7ffdf53db49d ntdll!RtlpAllocateHeapInternal+0x0000000000000a7d 7ffdf2dfdd3e ucrtbase!calloc_base+0x000000000000004e 7ffdf2dfdc74 ucrtbase!wsetlocale+0x0000000000000fc4 7ffdf2e0fa24 ucrtbase!initialize_narrow_environment+0x0000000000000074 7ffdf2e0f9c9 ucrtbase!initialize_narrow_environment+0x0000000000000019 7ffdf2e07730 ucrtbase!o__recalloc+0x0000000000000150 7ffdf2e06216 ucrtbase!msize+0x0000000000000146 7ffdf53c9a1d ntdll!LdrpCallInitRoutine+0x0000000000000061 7ffdf541d2f7 ntdll!LdrpInitializeNode+0x00000000000001d3 7ffdf541d08a ntdll!LdrpInitializeGraphRecurse+0x0000000000000042 7ffdf541d110 ntdll!LdrpInitializeGraphRecurse+0x00000000000000c8 7ffdf53ed947 ntdll!LdrpPrepareModuleForExecution+0x00000000000000bf 7ffdf53cfbae ntdll!LdrpLoadDllInternal+0x000000000000019a 7ffdf53c73e4 ntdll!LdrpLoadDll+0x00000000000000a8 7ffdf53c6af4 ntdll!LdrLoadDll+0x00000000000000e4 7ffdf2f22612 KERNELBASE!LoadLibraryExW+0x0000000000000162 7ff6139f2a86 aet_breakpad_test!google_breakpad::ExceptionHandler::Initialize+0x0000000000000516 7ff6139efb05 aet_breakpad_test!google_breakpad::ExceptionHandler::ExceptionHandler+0x00000000000000d5 7ff6139ec46c aet_breakpad_test!init_breakpad+0x00000000000000ac 7ff6139e4834 aet_breakpad_test!main+0x0000000000000044 7ff613a72619 aet_breakpad_test!invoke_main+0x0000000000000039 7ff613a724c2 aet_breakpad_test!__scrt_common_main_seh+0x0000000000000132 7ff613a7237e aet_breakpad_test!__scrt_common_main+0x000000000000000e 7ff613a726ae aet_breakpad_test!mainCRTStartup+0x000000000000000e 7ffdf41f7374 KERNEL32!BaseThreadInitThunk+0x0000000000000014 7ffdf53fcc91 ntdll!RtlUserThreadStart+0x0000000000000021 |
- 查看
10
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
0:000> !heap -flt s 10 _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cb0e20 0004 0000 [00] 0000000001cb0e50 00010 - (busy) 0000000001cb45f0 0004 0004 [00] 0000000001cb4620 00010 - (busy) 0000000001cb4970 0002 0004 [00] 0000000001cb4980 00010 - (free) 0000000001cb68b0 0002 0002 [00] 0000000001cb68c0 00010 - (free) 0000000001cc0280 0002 0002 [00] 0000000001cc0290 00010 - (free) 0000000001cc5d50 0002 0002 [00] 0000000001cc5d60 00010 - (free) 0000000001cc6e70 0002 0002 [00] 0000000001cc6e80 00010 - (free) 0000000001ccd030 0002 0002 [00] 0000000001ccd040 00010 - (free) 0000000001ccdd60 0004 0002 [00] 0000000001ccdd90 00010 - (busy) unknown!printable 0000000001ccde50 0004 0004 [00] 0000000001ccde80 00010 - (busy) ? dbghelp!RangeMapWrite+18c60 0000000001ccde90 0004 0004 [00] 0000000001ccdec0 00010 - (busy) ? dbghelp!RangeMapWrite+19118 0000000001ccded0 0004 0004 [00] 0000000001ccdf00 00010 - (busy) ? dbghelp!RangeMapWrite+191b8 0000000001ccdf10 0004 0004 [00] 0000000001ccdf40 00010 - (busy) ? dbghelp!RangeMapWrite+18b70 0000000001ccdf50 0004 0004 [00] 0000000001ccdf80 00010 - (busy) ? dbghelp!RangeMapWrite+188a8 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
0:000> !heap -p -a 0000000001ccdd60 address 0000000001ccdd60 found in _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001ccdd60 0004 0000 [00] 0000000001ccdd90 00010 - (busy) unknown!printable 7ffdf53db49d ntdll!RtlpAllocateHeapInternal+0x0000000000000a7d 7ffdf2dfdd3e ucrtbase!calloc_base+0x000000000000004e 7ffdf2dfdc74 ucrtbase!wsetlocale+0x0000000000000fc4 7ffdf2e0fa24 ucrtbase!initialize_narrow_environment+0x0000000000000074 7ffdf2e0f9c9 ucrtbase!initialize_narrow_environment+0x0000000000000019 7ffdf2e07730 ucrtbase!o__recalloc+0x0000000000000150 7ffdf2e06216 ucrtbase!msize+0x0000000000000146 7ffdf53c9a1d ntdll!LdrpCallInitRoutine+0x0000000000000061 7ffdf541d2f7 ntdll!LdrpInitializeNode+0x00000000000001d3 7ffdf541d08a ntdll!LdrpInitializeGraphRecurse+0x0000000000000042 7ffdf541d110 ntdll!LdrpInitializeGraphRecurse+0x00000000000000c8 7ffdf53ed947 ntdll!LdrpPrepareModuleForExecution+0x00000000000000bf 7ffdf53cfbae ntdll!LdrpLoadDllInternal+0x000000000000019a 7ffdf53c73e4 ntdll!LdrpLoadDll+0x00000000000000a8 7ffdf53c6af4 ntdll!LdrLoadDll+0x00000000000000e4 7ffdf2f22612 KERNELBASE!LoadLibraryExW+0x0000000000000162 7ff6139f2a86 aet_breakpad_test!google_breakpad::ExceptionHandler::Initialize+0x0000000000000516 7ff6139efb05 aet_breakpad_test!google_breakpad::ExceptionHandler::ExceptionHandler+0x00000000000000d5 7ff6139ec46c aet_breakpad_test!init_breakpad+0x00000000000000ac 7ff6139e4834 aet_breakpad_test!main+0x0000000000000044 7ff613a72619 aet_breakpad_test!invoke_main+0x0000000000000039 7ff613a724c2 aet_breakpad_test!__scrt_common_main_seh+0x0000000000000132 7ff613a7237e aet_breakpad_test!__scrt_common_main+0x000000000000000e 7ff613a726ae aet_breakpad_test!mainCRTStartup+0x000000000000000e 7ffdf41f7374 KERNEL32!BaseThreadInitThunk+0x0000000000000014 7ffdf53fcc91 ntdll!RtlUserThreadStart+0x0000000000000021 |
- 查看
50
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 |
0:000> !heap -flt s 50 _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cb3a70 0008 0000 [00] 0000000001cb3aa0 00050 - (busy) 0000000001cb3c40 0008 0008 [00] 0000000001cb3c70 00050 - (busy) 0000000001cb3f20 0008 0008 [00] 0000000001cb3f50 00050 - (busy) 0000000001cb4180 0008 0008 [00] 0000000001cb41b0 00050 - (busy) 0000000001cb4850 0008 0008 [00] 0000000001cb4880 00050 - (busy) 0000000001cb4a40 0008 0008 [00] 0000000001cb4a70 00050 - (busy) 0000000001cb5410 0008 0008 [00] 0000000001cb5440 00050 - (busy) 0000000001cbe3c0 0008 0008 [00] 0000000001cbe3f0 00050 - (busy) ? ntdll!RtlpFlsContext+48 0000000001cbe440 0008 0008 [00] 0000000001cbe470 00050 - (busy) unknown!noop 0000000001cbe5c0 0008 0008 [00] 0000000001cbe5f0 00050 - (busy) 0000000001cbe6c0 0008 0008 [00] 0000000001cbe6f0 00050 - (busy) 0000000001cbedc0 0008 0008 [00] 0000000001cbedf0 00050 - (busy) 0000000001cbf040 0008 0008 [00] 0000000001cbf070 00050 - (busy) 0000000001cbf0c0 0008 0008 [00] 0000000001cbf0f0 00050 - (busy) 0000000001cc1840 0008 0008 [00] 0000000001cc1870 00050 - (busy) 0000000001cccbb0 0006 0008 [00] 0000000001cccbc0 00050 - (free) 0000000001cce700 0006 0006 [00] 0000000001cce710 00050 - (free) 0000000001cce7c0 0006 0006 [00] 0000000001cce7d0 00050 - (free) 0000000001cce820 0006 0006 [00] 0000000001cce830 00050 - (free) 0000000001cce8e0 0006 0006 [00] 0000000001cce8f0 00050 - (free) 0000000001cce9a0 0006 0006 [00] 0000000001cce9b0 00050 - (free) 0000000001ccea60 0006 0006 [00] 0000000001ccea70 00050 - (free) 0000000001cceac0 0006 0006 [00] 0000000001ccead0 00050 - (free) 0000000001cceb20 0006 0006 [00] 0000000001cceb30 00050 - (free) 0000000001cceb80 0006 0006 [00] 0000000001cceb90 00050 - (free) 0000000001ccebe0 0006 0006 [00] 0000000001ccebf0 00050 - (free) 0000000001ccec40 0006 0006 [00] 0000000001ccec50 00050 - (free) 0000000001cced60 0006 0006 [00] 0000000001cced70 00050 - (free) 0000000001ccedc0 0006 0006 [00] 0000000001ccedd0 00050 - (free) 0000000001ccee20 0006 0006 [00] 0000000001ccee30 00050 - (free) 0000000001ccee80 0006 0006 [00] 0000000001ccee90 00050 - (free) 0000000001ccef40 0006 0006 [00] 0000000001ccef50 00050 - (free) 0000000001ccf120 0006 0006 [00] 0000000001ccf130 00050 - (free) 0000000001ccf180 0006 0006 [00] 0000000001ccf190 00050 - (free) 0000000001ccf1e0 0006 0006 [00] 0000000001ccf1f0 00050 - (free) 0000000001ccf360 0006 0006 [00] 0000000001ccf370 00050 - (free) 0000000001ccf480 0006 0006 [00] 0000000001ccf490 00050 - (free) 0000000001ccf4e0 0006 0006 [00] 0000000001ccf4f0 00050 - (free) _HEAP @ 10000 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
0:000> !heap -p -a 0000000001cc1840 address 0000000001cc1840 found in _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cc1840 0008 0000 [00] 0000000001cc1870 00050 - (busy) 7ffdf53db49d ntdll!RtlpAllocateHeapInternal+0x0000000000000a7d 7ff613a9bd35 aet_breakpad_test!heap_alloc_dbg_internal+0x0000000000000205 7ff613a9bfcd aet_breakpad_test!heap_alloc_dbg+0x000000000000004d 7ff613a9b2cc aet_breakpad_test!_calloc_dbg+0x000000000000006c 7ff613b15316 aet_breakpad_test!create_environment<char>+0x00000000000000f6 7ff613b14e5f aet_breakpad_test!common_initialize_environment_nolock<char>+0x000000000000006f 7ff613b164f9 aet_breakpad_test!_initialize_narrow_environment+0x0000000000000009 7ff613a725c9 aet_breakpad_test!__scrt_narrow_environment_policy::initialize_environment+0x0000000000000009 7ff613a722ca aet_breakpad_test!pre_c_initialization+0x000000000000009a 7ff613b16608 aet_breakpad_test!_initterm_e+0x0000000000000058 7ff613a723fa aet_breakpad_test!__scrt_common_main_seh+0x000000000000006a 7ff613a7237e aet_breakpad_test!__scrt_common_main+0x000000000000000e 7ff613a726ae aet_breakpad_test!mainCRTStartup+0x000000000000000e 7ffdf41f7374 KERNEL32!BaseThreadInitThunk+0x0000000000000014 7ffdf53fcc91 ntdll!RtlUserThreadStart+0x0000000000000021 |
- 查看
30
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
0:000> !heap -flt s 30 _HEAP @ 1cb0000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001cb0740 0006 0000 [00] 0000000001cb0770 00030 - (busy) 0000000001cb3830 0006 0006 [00] 0000000001cb3860 00030 - (busy) unknown!noop 0000000001cb3fa0 0006 0006 [00] 0000000001cb3fd0 00030 - (busy) 0000000001cb4630 0006 0006 [00] 0000000001cb4660 00030 - (busy) 0000000001cb4690 0007 0006 [00] 0000000001cb46c0 00030 - (busy) 0000000001cb5520 0006 0007 [00] 0000000001cb5550 00030 - (busy) 0000000001cb56b0 0006 0006 [00] 0000000001cb56e0 00030 - (busy) 0000000001cb5710 0006 0006 [00] 0000000001cb5740 00030 - (busy) 0000000001cb58d0 0006 0006 [00] 0000000001cb5900 00030 - (busy) 0000000001cb6070 0006 0006 [00] 0000000001cb60a0 00030 - (busy) ? ntdll!RtlpFcProcessManager+d8 0000000001cb73c0 0006 0006 [00] 0000000001cb73f0 00030 - (busy) 0000000001cb7420 0006 0006 [00] 0000000001cb7450 00030 - (busy) 0000000001cb7480 0006 0006 [00] 0000000001cb74b0 00030 - (busy) 0000000001cb74e0 0006 0006 [00] 0000000001cb7510 00030 - (busy) 0000000001cb7540 0006 0006 [00] 0000000001cb7570 00030 - (busy) 0000000001cb9ad0 0006 0006 [00] 0000000001cb9b00 00030 - (busy) 0000000001cb9b30 0006 0006 [00] 0000000001cb9b60 00030 - (busy) 0000000001cb9b90 0006 0006 [00] 0000000001cb9bc0 00030 - (busy) 0000000001cb9bf0 0006 0006 [00] 0000000001cb9c20 00030 - (busy) 0000000001cb9c50 0006 0006 [00] 0000000001cb9c80 00030 - (busy) 0000000001cb9cb0 0006 0006 [00] 0000000001cb9ce0 00030 - (busy) 0000000001cb9d10 0006 0006 [00] 0000000001cb9d40 00030 - (busy) 0000000001cb9d70 0006 0006 [00] 0000000001cb9da0 00030 - (busy) 0000000001cb9dd0 0006 0006 [00] 0000000001cb9e00 00030 - (busy) 0000000001cb9e30 0006 0006 [00] 0000000001cb9e60 00030 - (busy) 0000000001cb9e90 0006 0006 [00] 0000000001cb9ec0 00030 - (busy) 0000000001cb9ef0 0006 0006 [00] 0000000001cb9f20 00030 - (busy) 0000000001cb9f50 0006 0006 [00] 0000000001cb9f80 00030 - (busy) // 忽略部分数据 0000000001ccf300 0006 0006 [00] 0000000001ccf330 00030 - (busy) 0000000001ccf3c0 0006 0006 [00] 0000000001ccf3f0 00030 - (busy) 0000000001ccf420 0006 0006 [00] 0000000001ccf450 00030 - (busy) 0000000001ccf540 0006 0006 [00] 0000000001ccf570 00030 - (busy) 0000000001cd3830 0004 0006 [00] 0000000001cd3840 00030 - (free) 0000000001cd3870 0004 0004 [00] 0000000001cd3880 00030 - (free) 0000000001cd38b0 0004 0004 [00] 0000000001cd38c0 00030 - (free) 0000000001cd38f0 0004 0004 [00] 0000000001cd3900 00030 - (free) 0000000001cd3930 0004 0004 [00] 0000000001cd3940 00030 - (free) 0000000001cd39b0 0004 0004 [00] 0000000001cd39c0 00030 - (free) // 忽略部分数据 0000000001cd45f0 0004 0004 [00] 0000000001cd4600 00030 - (free) 0000000001cd4630 0004 0004 [00] 0000000001cd4640 00030 - (free) 0000000001cd4670 0004 0004 [00] 0000000001cd4680 00030 - (free) _HEAP @ 10000 |
- 通过
!heap -stat -h 1cb0000看到的很多地址经过详细查看后,并不是我的目标模块 - 这个时候准备使用别的方案
验证二
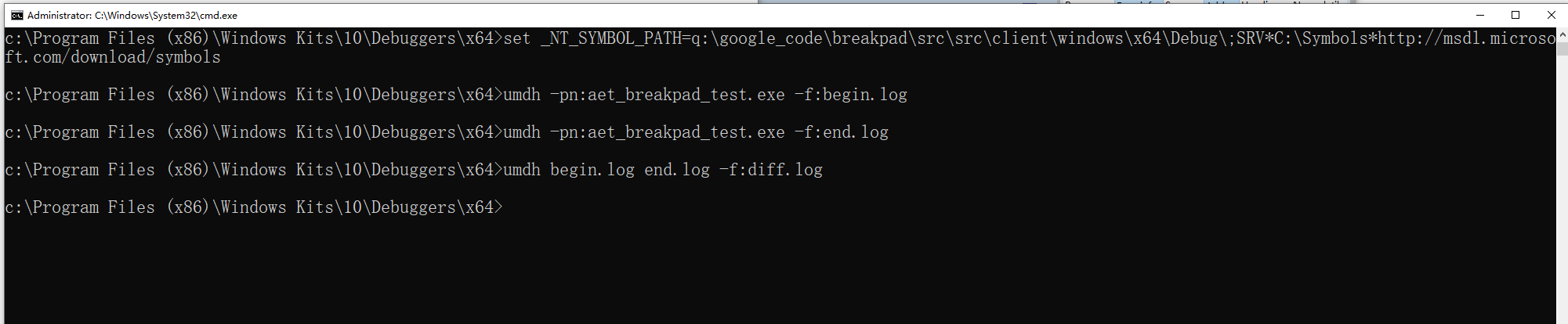
- 使用了
UMDH,来查看快照
begin.log
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 |
// // UMDH: Logtime 2025-03-29 15:16 - Machine=DESKTOP-NRIG174 - PID=23956 // // Debug privilege has been enabled. // OS version 10.0 // // Preparing to dump heap allocations. // Only allocations for which the heap manager collected a stack are dumped. Allocations whithout stack are ignored. // The stack trace for an allocation is dumped as a list of addresses. They will be resolved to function names at compare time. // // Connecting to process 23956 ... // Process 23956 opened handle=260. // // Loaded modules and symbol info: // Base Size ModuleName*ModuleTimeStamp*PdbName*PdbId*PdbAge // 7FF613900000 2F7000 Q:\google_code\breakpad\src\src\client\windows\x64\Debug\aet_breakpad_test.exe*67e67e15*Q:\google_code\breakpad\src\src\client\windows\x64\Debug\aet_breakpad_test.pdb*43e7b8333335468aa4eb0fdb811507b6*3 // 7FFDF53B0000 1F8000 C:\Windows\SYSTEM32\ntdll.dll*ab0dece3*ntdll.pdb*9ff79bba19ebed309623072ea067b20f*1 // 7FFDF41E0000 C2000 C:\Windows\System32\KERNEL32.DLL*5c4539f7*kernel32.pdb*8b1f388f8424b0d61154bc25b96f3792*1 // 7FFDF2EF0000 2FF000 C:\Windows\System32\KERNELBASE.dll*9ce69c7*kernelbase.pdb*6d34aca37853a408fddd2bfe0fc1c19c*1 // // Loaded modules: // Base Size Module // 7FF613900000 2F7000 Q:\google_code\breakpad\src\src\client\windows\x64\Debug\aet_breakpad_test.exe // 7FFDF53B0000 1F8000 C:\Windows\SYSTEM32\ntdll.dll // 7FFDF41E0000 C2000 C:\Windows\System32\KERNEL32.DLL // 7FFDF2EF0000 2FF000 C:\Windows\System32\KERNELBASE.dll // // Process modules enumerated. // Debug library initialized ... 7FFDF53B0000-7FFDF55A7FFF DBGHELP: ntdll - public symbols C:\Symbols\ntdll.pdb\9FF79BBA19EBED309623072EA067B20F1\ntdll.pdb *- - - - - - - - - - Start of data for heap @ 1C40000 - - - - - - - - - - REQUESTED bytes + OVERHEAD at ADDRESS by BackTraceID STACK if not already dumped. *- - - - - - - - - - Heap 1C40000 Hogs - - - - - - - - - - 100 bytes + 50 at 1C408A0 by BackTrace1920C0 7FFDF53DB49D 7FFDF53F31ED 7FFDF53F30AB 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 1D8 bytes + 58 at 1C409F0 by BackTrace192180 7FFDF53DB49D 7FFDF53BDFCC 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 1D8 bytes + 58 at 1C40C20 by BackTrace192240 7FFDF53DB49D 7FFDF5412DAD 7FFDF53C388C 7FFDF53C2634 7FFDF53C22CD 7FFDF53C09A3 7FFDF53BE02C 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 48 bytes + 58 at 1C40E50 by BackTrace192380 7FFDF53DB49D 7FFDF5412DF7 7FFDF53C388C 7FFDF53C2634 7FFDF53C22CD 7FFDF53C09A3 7FFDF53BE02C 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 4 bytes + 5C at 1C40EF0 by BackTrace1924C0 7FFDF53DB49D 7FFDF5412EA3 7FFDF53C388C 7FFDF53C2634 7FFDF53C22CD 7FFDF53C09A3 7FFDF53BE02C 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E // 忽略一部分数据 F0 bytes + 50 at 1C47C70 by BackTrace198E80 7FFDF53DB49D 7FFDF53BF372 7FFDF5412BCE 7FFDF5483B18 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E *- - - - - - - - - - End of data for heap @ 1C40000 - - - - - - - - - - *- - - - - - - - - - Start of data for heap @ 10000 - - - - - - - - - - REQUESTED bytes + OVERHEAD at ADDRESS by BackTraceID STACK if not already dumped. *- - - - - - - - - - Heap 10000 Hogs - - - - - - - - - - *- - - - - - - - - - End of data for heap @ 10000 - - - - - - - - - - |
end.log
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 |
// // UMDH: Logtime 2025-03-29 15:17 - Machine=DESKTOP-NRIG174 - PID=23956 // // Debug privilege has been enabled. // OS version 10.0 // // Preparing to dump heap allocations. // Only allocations for which the heap manager collected a stack are dumped. Allocations whithout stack are ignored. // The stack trace for an allocation is dumped as a list of addresses. They will be resolved to function names at compare time. // // Connecting to process 23956 ... // Process 23956 opened handle=260. // // Loaded modules and symbol info: // Base Size ModuleName*ModuleTimeStamp*PdbName*PdbId*PdbAge // 7FF613900000 2F7000 Q:\google_code\breakpad\src\src\client\windows\x64\Debug\aet_breakpad_test.exe*67e67e15*Q:\google_code\breakpad\src\src\client\windows\x64\Debug\aet_breakpad_test.pdb*43e7b8333335468aa4eb0fdb811507b6*3 // 7FFDF53B0000 1F8000 C:\Windows\SYSTEM32\ntdll.dll*ab0dece3*ntdll.pdb*9ff79bba19ebed309623072ea067b20f*1 // 7FFDF41E0000 C2000 C:\Windows\System32\KERNEL32.DLL*5c4539f7*kernel32.pdb*8b1f388f8424b0d61154bc25b96f3792*1 // 7FFDF2EF0000 2FF000 C:\Windows\System32\KERNELBASE.dll*9ce69c7*kernelbase.pdb*6d34aca37853a408fddd2bfe0fc1c19c*1 // 7FFDE4F30000 1E4000 C:\Windows\SYSTEM32\dbghelp.dll*9a866525*dbghelp.pdb*961ac3bbb51c2d60a763d5fd89f820a7*1 // 7FFDF2DF0000 100000 C:\Windows\System32\ucrtbase.dll*81cf5d89*ucrtbase.pdb*5c4f64bf99f5fdec7295cab05a30010d*1 // 7FFDD56B0000 34000 C:\Windows\SYSTEM32\dbgcore.DLL*a4254c09*dbgcore.pdb*6a072ad6b41ec0723dc8d38fdb3bae92*1 // 7FFDF4C80000 123000 C:\Windows\System32\rpcrt4.dll*782a457b*rpcrt4.pdb*152bd4e8ac31a21fce1cb8eec5221fd3*1 // 7FFDF2A80000 82000 C:\Windows\System32\bcryptPrimitives.dll*c54120ed*bcryptprimitives.pdb*9025181284470d297546974ad8e6867a*1 // // Loaded modules: // Base Size Module // 7FF613900000 2F7000 Q:\google_code\breakpad\src\src\client\windows\x64\Debug\aet_breakpad_test.exe // 7FFDF53B0000 1F8000 C:\Windows\SYSTEM32\ntdll.dll // 7FFDF41E0000 C2000 C:\Windows\System32\KERNEL32.DLL // 7FFDF2EF0000 2FF000 C:\Windows\System32\KERNELBASE.dll // 7FFDE4F30000 1E4000 C:\Windows\SYSTEM32\dbghelp.dll // 7FFDF2DF0000 100000 C:\Windows\System32\ucrtbase.dll // 7FFDD56B0000 34000 C:\Windows\SYSTEM32\dbgcore.DLL // 7FFDF4C80000 123000 C:\Windows\System32\rpcrt4.dll // 7FFDF2A80000 82000 C:\Windows\System32\bcryptPrimitives.dll // // Process modules enumerated. // Debug library initialized ... 7FFDF53B0000-7FFDF55A7FFF DBGHELP: ntdll - public symbols C:\Symbols\ntdll.pdb\9FF79BBA19EBED309623072EA067B20F1\ntdll.pdb *- - - - - - - - - - Start of data for heap @ 1C40000 - - - - - - - - - - REQUESTED bytes + OVERHEAD at ADDRESS by BackTraceID STACK if not already dumped. *- - - - - - - - - - Heap 1C40000 Hogs - - - - - - - - - - 100 bytes + 50 at 1C408A0 by BackTrace1920C0 7FFDF53DB49D 7FFDF53F31ED 7FFDF53F30AB 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 1D8 bytes + 58 at 1C409F0 by BackTrace192180 7FFDF53DB49D 7FFDF53BDFCC 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 1D8 bytes + 58 at 1C40C20 by BackTrace192240 7FFDF53DB49D 7FFDF5412DAD 7FFDF53C388C 7FFDF53C2634 7FFDF53C22CD 7FFDF53C09A3 7FFDF53BE02C 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 48 bytes + 58 at 1C40E50 by BackTrace192380 7FFDF53DB49D 7FFDF5412DF7 7FFDF53C388C 7FFDF53C2634 7FFDF53C22CD 7FFDF53C09A3 7FFDF53BE02C 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 4 bytes + 5C at 1C40EF0 by BackTrace1924C0 7FFDF53DB49D 7FFDF5412EA3 7FFDF53C388C 7FFDF53C2634 7FFDF53C22CD 7FFDF53C09A3 7FFDF53BE02C 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 10 bytes + 50 at 1C40F50 by BackTrace192600 7FFDF53DB49D 7FFDF5412EE1 7FFDF53C388C 7FFDF53C2634 7FFDF53C22CD 7FFDF53C09A3 7FFDF53BE02C 7FFDF542E41E 7FFDF53F38C0 7FFDF53F2F43 7FFDF53F30E5 7FFDF53F2EA0 7FFDF5482878 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 100 bytes + 50 at 1C40FB0 by BackTrace1929C0 7FFDF53DB49D 7FFDF53F31ED 7FFDF53F30AB 7FFDF53F2EA0 7FFDF5482895 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 100 bytes + 50 at 1C41100 by BackTrace192A80 7FFDF53DB49D 7FFDF53F31ED 7FFDF53F30AB 7FFDF53F2EA0 7FFDF54828B2 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E 2064 bytes + 5C at 1C41250 by BackTrace192B40 7FFDF53DB49D 7FFDF53FB001 7FFDF54828CC 7FFDF5425DEB 7FFDF5425C73 7FFDF5425C1E // 忽略一部分数据 18C bytes + 54 at 1C66540 by BackTrace1F2520 7FFDF53DB49D 7FF613A9BD35 7FF613A9BFCD 7FF613A9B2CC 7FF613B17FE0 7FF613B1768D 7FF613B178E9 7FF613B1A2B1 7FF613AF8A0A 7FF613AF827E 7FF613AF8056 7FF613AF8117 7FF613AF8AD3 7FF6139F90EC 7FF6139E050C 7FF6139E6D85 7FF6139E1704 7FF6139E786A 7FF6139EA54C 7FF6139ED016 7FF613A1B89A 7FF6139E485C 7FF613A72619 7FF613A724C2 7FF613A7237E 7FF613A726AE 7FFDF41F7374 7FFDF53FCC91 *- - - - - - - - - - End of data for heap @ 1C40000 - - - - - - - - - - *- - - - - - - - - - Start of data for heap @ 10000 - - - - - - - - - - REQUESTED bytes + OVERHEAD at ADDRESS by BackTraceID STACK if not already dumped. *- - - - - - - - - - Heap 10000 Hogs - - - - - - - - - - *- - - - - - - - - - End of data for heap @ 10000 - - - - - - - - - - |
diff.log- 从对比结果的大量数据中,使用
aet_breakpad_test!operator new+或者aet_breakpad_test!operator new+13搜索 - 找到了
16条 - 挨个得查看,最后发现了自己模块中分配内存的一条,如下
- 从对比结果的大量数据中,使用
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
+ 5c ( 5c - 0) 1 allocs BackTrace1F3960 + 1 ( 1 - 0) BackTrace1F3960 allocations ntdll!RtlpAllocateHeapInternal+A7D aet_breakpad_test!heap_alloc_dbg_internal+205 (minkernel\crts\ucrt\src\appcrt\heap\debug_heap.cpp, 359) aet_breakpad_test!heap_alloc_dbg+4D (minkernel\crts\ucrt\src\appcrt\heap\debug_heap.cpp, 450) aet_breakpad_test!_malloc_dbg+2F (minkernel\crts\ucrt\src\appcrt\heap\debug_heap.cpp, 496) aet_breakpad_test!malloc+1E (minkernel\crts\ucrt\src\appcrt\heap\malloc.cpp, 27) aet_breakpad_test!operator new+13 (D:\a\_work\1\s\src\vctools\crt\vcstartup\src\heap\new_scalar.cpp, 36) aet_breakpad_test!operator new[]+13 (D:\a\_work\1\s\src\vctools\crt\vcstartup\src\heap\new_array.cpp, 30) aet_breakpad_test!main+94 (Q:\google_code\breakpad\src\src\client\windows\aet_test\aet_breakpad_test\aet_breakpad_test.cpp, 52) aet_breakpad_test!invoke_main+39 (D:\a\_work\1\s\src\vctools\crt\vcstartup\src\startup\exe_common.inl, 79) aet_breakpad_test!__scrt_common_main_seh+132 (D:\a\_work\1\s\src\vctools\crt\vcstartup\src\startup\exe_common.inl, 288) aet_breakpad_test!__scrt_common_main+E (D:\a\_work\1\s\src\vctools\crt\vcstartup\src\startup\exe_common.inl, 331) aet_breakpad_test!mainCRTStartup+E (D:\a\_work\1\s\src\vctools\crt\vcstartup\src\startup\exe_main.cpp, 17) KERNEL32!BaseThreadInitThunk+14 ntdll!RtlUserThreadStart+21 |
验证三
- 从验证二里面,定位了目标块
5c - 在
windbg里面再次验证
|
1 2 3 4 5 6 7 |
0:000> !heap -flt s 5c _HEAP @ 1c40000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001c4caa0 000b 0000 [00] 0000000001c4cad0 0005c - (busy) 0000000001c4fa60 000b 000b [00] 0000000001c4fa90 0005c - (busy) 0000000001c66240 000b 000b [00] 0000000001c66270 0005c - (busy) _HEAP @ 10000 |
- 逐条查看
- 第三条内容如下:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
0:000> !heap -p -a 0000000001c66240 address 0000000001c66240 found in _HEAP @ 1c40000 HEAP_ENTRY Size Prev Flags UserPtr UserSize - state 0000000001c66240 000b 0000 [00] 0000000001c66270 0005c - (busy) 7ffdf53db49d ntdll!RtlpAllocateHeapInternal+0x0000000000000a7d 7ff613a9bd35 aet_breakpad_test!heap_alloc_dbg_internal+0x0000000000000205 7ff613a9bfcd aet_breakpad_test!heap_alloc_dbg+0x000000000000004d 7ff613a9b4df aet_breakpad_test!_malloc_dbg+0x000000000000002f 7ff613b1234e aet_breakpad_test!malloc+0x000000000000001e 7ff613a71b33 aet_breakpad_test!operator new+0x0000000000000013 7ff6139dde43 aet_breakpad_test!operator new[]+0x0000000000000013 7ff6139e4884 aet_breakpad_test!main+0x0000000000000094 7ff613a72619 aet_breakpad_test!invoke_main+0x0000000000000039 7ff613a724c2 aet_breakpad_test!__scrt_common_main_seh+0x0000000000000132 7ff613a7237e aet_breakpad_test!__scrt_common_main+0x000000000000000e 7ff613a726ae aet_breakpad_test!mainCRTStartup+0x000000000000000e 7ffdf41f7374 KERNEL32!BaseThreadInitThunk+0x0000000000000014 7ffdf53fcc91 ntdll!RtlUserThreadStart+0x0000000000000021 |
总结
- 经过了验证二和验证三,可以确定是
main函数52行这里的问题
其他总结
!heap -stat -h 1cb0000的排序
- 这些排序好像并没有升序的方法
-grp G- 表示 按全局标签(
Global Tags) 对内存分配进行分类统计 - 全局标签是堆分配时附加的元数据,常用于标记内存用途(如线程池、缓存等)
- 通过
G分组,可快速识别不同标签下的内存使用情况
- 表示 按全局标签(
|
1 2 3 4 5 6 7 8 9 |
0:000> !heap -stat -h 1c40000 -grp G 5 heap @ 0000000001c40000 group-by: TOTSIZE max-display: 5 size #blocks total ( %) (percent of total busy bytes) 30 cb - 2610 (10.77) 2064 1 - 2064 (9.17) 10 12f - 12f0 (5.36) 1234 1 - 1234 (5.15) 1200 1 - 1200 (5.09) |
-grp A- 按分配大小分组
- 统计不同内存块大小的分配情况(如
16B、32B、64B等) - 适用场景:分析内存碎片化问题或高频分配的小对象
|
1 2 3 4 5 6 7 8 9 10 11 12 |
0:000> !heap -stat -h 1c40000 -grp A 8 heap @ 0000000001c40000 group-by: ALLOCATIONSIZE max-display: 8 size #blocks total ( %) (percent of total busy bytes) 2064 1 - 2064 (9.17) 1234 1 - 1234 (5.15) 1200 1 - 1200 (5.09) 1034 1 - 1034 (4.58) 1000 1 - 1000 (4.53) ed6 1 - ed6 (4.20) 844 1 - 844 (2.34) 790 2 - f20 (4.28) |
-grp B- 按块数量分组
- 统计每个分配大小对应的内存块数量
- 适用场景:识别内存分配频率最高的尺寸类别
|
1 2 3 4 5 6 7 8 9 10 11 12 |
0:000> !heap -stat -h 1c40000 -grp B 8 heap @ 0000000001c40000 group-by: BLOCKCOUNT max-display: 8 size #blocks total ( %) (percent of totalblocks) 10 12f - 12f0 (39.25) 30 cb - 2610 (26.30) 50 f - 4b0 (1.94) 44 d - 374 (1.68) 100 a - a00 (1.30) 120 9 - a20 (1.17) 40 9 - 240 (1.17) 52 6 - 1ec (0.78) |
-grp S- 按总分配大小分组
- 统计每个分配大小对应的总内存占用
- 适用场景:定位内存消耗最大的尺寸类别
|
1 2 3 4 5 6 7 8 9 10 11 12 |
0:000> !heap -stat -h 1c40000 -grp S 8 heap @ 0000000001c40000 group-by: TOTSIZE max-display: 8 size #blocks total ( %) (percent of total busy bytes) 30 cb - 2610 (10.77) 2064 1 - 2064 (9.17) 10 12f - 12f0 (5.36) 1234 1 - 1234 (5.15) 1200 1 - 1200 (5.09) 1034 1 - 1034 (4.58) 1000 1 - 1000 (4.53) 790 2 - f20 (4.28) |
本文为原创文章,版权归Aet所有,欢迎分享本文,转载请保留出处!
你可能也喜欢
- ♥ Cef:介绍06/29
- ♥ Bkwin一12/01
- ♥ Windows 核心编程 _ 用户模式:线程同步二07/16
- ♥ Soui应用 动画一06/24
- ♥ Soui九07/25
- ♥ Windows进程通信相关03/10